| https://twitter.com/mwulftange |
Markus Wulftange
- 67 Followers
- 35 Following
- 20 Posts
From: @codewhitesec
https://infosec.exchange/@codewhitesec/114241026482611250
CODE WHITE GmbH (@codewhitesec@infosec.exchange)
Our crew members @mwulftange & @frycos discovered & responsibly disclosed several new RCE gadgets that bypass #Veeam's blacklist for CVE-2024-40711 & CVE-2025-23120 as well as further entry points following @SinSinology & @chudypb 's blog. Don’t blacklist - replace BinaryFormatter.
CODE WHITE | Teaching the Old .NET Remoting New Exploitation Tricks
This blog post provides insights into three exploitation techniques that can still be used in cases of a hardened .NET Remoting server with `TypeFilterLevel.Low` and Code Access Security (CAS) restrictions in place. Two of these tricks are considered novel and can help in cases where ExploitRemotingService is stuck.
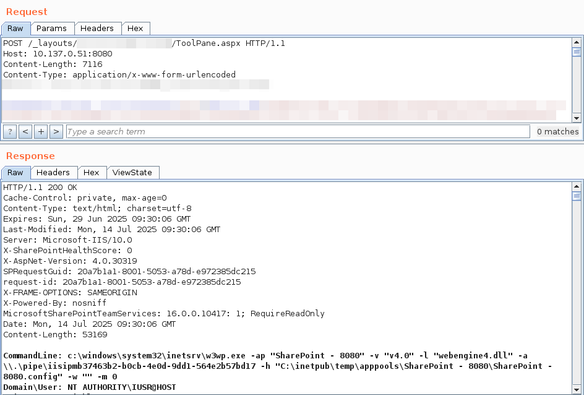
Our second blog post about ASP .NET TemplateParser exploitation is live: @mwulftange unveils how a novel bypass technique can be applied to get RCE in SharePoint Online & On-Premise (CVE-2023-33160)
https://code-white.com/blog/exploiting-asp.net-templateparser-part-2/
CODE WHITE | Exploiting ASP.NET TemplateParser — Part II: SharePoint (CVE-2023-33160)
In Part I, we dug into the internals of the ASP.NET `TemplateParser` and elaborated its capabilities in respect to exploitation. In this part, we will look into whether and how this can also be exploited to gain Remote Code Execution. While this research was originally focussed on the `TemplateParser`, the newly discovered technique was also applicable to SharePoint on-premises and SharePoint Online. So we'll elaborate on how SharePoint protects against the use of malicious code and will present a novel trick that allowed to bypass these security measures (CVE-2023-33160).