If you need to identify #malware quickly, give #malcat a try: its Kesakode code identification is fast and can even work offline!
More info: https://doc.malcat.fr/analysis/kesakode.html
| Website | https://malcat.fr |
| https://twitter.com/malcat4ever | |
| https://www.linkedin.com/company/malcat | |
| Discord | https://discord.gg/Pf3s2ZKqtU |
If you need to identify #malware quickly, give #malcat a try: its Kesakode code identification is fast and can even work offline!
More info: https://doc.malcat.fr/analysis/kesakode.html
Does someone know this #malware, since this is definitely NOT latrodectus. Looks like some Discord-backed infostealer:
https://bazaar.abuse.ch/sample/85f8ccf69bed672d92b40c45f9571378a7d00c80b86004a76018d9e120eeaa01/
You can now check your strings in #malcat against an online library of #Malpedia FLOSSed strings. Just copy this plugin:
https://github.com/malpedia/malpedia-flossed?tab=readme-ov-file#plugin-for-malcat
#Malcat 0.9.10 is out! State-of-the-art CFG recovery, MIPS disassembler & decompiler and many UI improvements;
https://malcat.fr/blog/0910-is-out-cfg-recovery-mips-ui-improvements
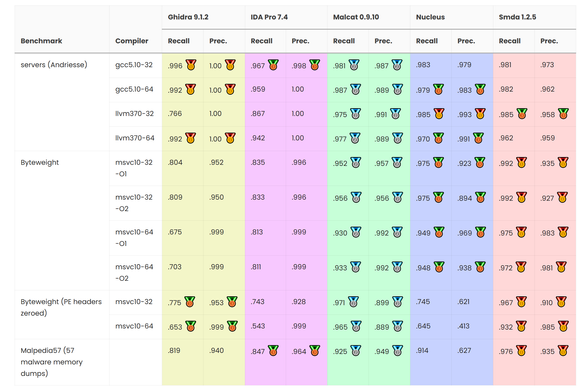
Malcat version 0.9.10 is out! In this release, we have improved Malcat's CFG recovery algorithm and compared its performances against other reversing software. A new CPU architecture (MIPS) has also been added and multiple improvements to the decompiler interface in Malcat were made. Last but not least, several QoL changes have been made, from a new preview popup in data and code views to new scripts/transform and an more extensive corpus search.
#Malcat 0.9.10 is out! State-of-the-art CFG recovery, MIPS disassembler & decompiler and many UI improvements;
https://malcat.fr/blog/0910-is-out-cfg-recovery-mips-ui-improvements

Malcat version 0.9.10 is out! In this release, we have improved Malcat's CFG recovery algorithm and compared its performances against other reversing software. A new CPU architecture (MIPS) has also been added and multiple improvements to the decompiler interface in Malcat were made. Last but not least, several QoL changes have been made, from a new preview popup in data and code views to new scripts/transform and an more extensive corpus search.
Malcat version 0.9.9 is out! Check out the new offline version of Kesakode for blazing-fast (unpacked) #malware identification across 2000+ families.
Also python 3.13 support (& disassembler), new file parsers & improved UI:
https://malcat.fr/blog/099-is-out-offline-kesakode-python-313-ui
Malcat version 0.9.9 is out! Say hello to the offline version of Kesakode, which lets you identify malware even faster and without uploading any hash! You will also see several UI improvements, python 3.13 support and a couple of optimisations regarding file parsers. Last but not least, the threat intelligence features are now available in the lite edition!
Malcat tip #9: So you have found this nice #malware hash in a report, but no sample?
"File>Download from hash" will retrieve the hash for you from:
● Triage
● MalwareBazaar
● VirusShare
● MWDB
● FileScanIO
NB: some of these sources require (free) API keys.
Malcat 0.9.8 is out! You'll find a lot of QoL improvements, improved API and more doc. More infos:
https://malcat.fr/blog/098-is-out-scripting-qol-improvements/