| WIRED | https://www.wired.com/author/lily-hay-newman/ |
Lily Hay Newman
- 4.3K Followers
- 299 Following
- 112 Posts
Drop what you are doing and read this incredible story from Wired, if you can. After that, come back here.
https://www.wired.com/story/edward-coristine-tesla-sexy-path-networks-doge/
It mentions that a 19 y/o man who's assisting Musk's team and who has access to sensitive government systems is Edward Coristine. Wired said Coristine, who apparently goes by the nickname "Big Balls," runs a number of companies, including one called Tesla.Sexy LLC
"Tesla.Sexy controls dozens of web domains, including at least two Russian-registered domains. One of those domains, which is still active, offers a service called Helfie, which is an AI bot for Discord servers targeting the Russian market.While the operation of a Russian website would not violate US sanctions preventing Americans doing business with Russian companies, it could potentially be a factor in a security clearance review."
The really interesting part for me is Coristine's work history at a company called Path Networks, which Wired describes generously as a company "known for hiring reformed black-hat hackers."
"At Path Network, Coristine worked as a systems engineer from April to June of 2022, according to his now-deleted LinkedIn resume. Path has at times listed as employees Eric Taylor, also known as Cosmo the God, a well-known former cybercriminal and member of the hacker group UGNazis, as well as Matthew Flannery, an Australian convicted hacker whom police allege was a member of the hacker group LulzSec. It’s unclear whether Coristine worked at Path concurrently with those hackers, and WIRED found no evidence that either Coristine or other Path employees engaged in illegal activity while at the company."
The founder of Path is a young man named Marshal Webb. I wrote about Webb back in 2016, in a story about a DDoS defense company he co-founded called BackConnect LLC. Working with Doug Madory, we determined that BackConnect had a long history of hijacking Internet address space that it didn't own.
https://krebsonsecurity.com/2016/09/ddos-mitigation-firm-has-history-of-hijacks/
Incidentally, less than 24 hours after that story ran, my site KrebsOnSecurity.com was hit with the biggest DDoS attack the Internet had ever seen at the time. That sustained attack kept my site offline for nearly 4 days.
https://krebsonsecurity.com/2016/09/krebsonsecurity-hit-with-record-ddos/
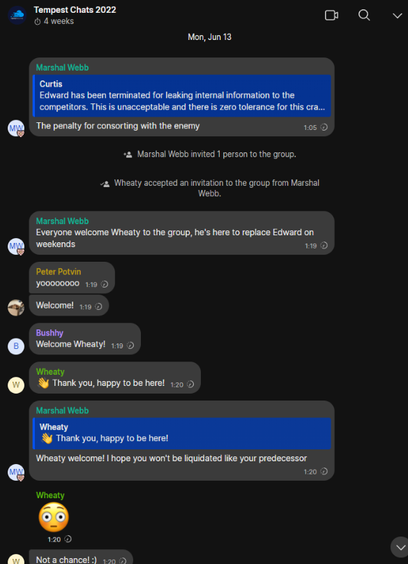
Here's the real story behind why Coristine only worked at Path for a few months. He was fired after Webb accused him of making it known that one of Path's employees was Curtis Gervais, a serial swatter from Canada who was convicted of perpetrating dozens of swattings and bomb threats -- including at least two attempts on our home in 2014. [BTW the aforementioned Eric Taylor was convicted of a separate (successful) swatting against our home in 2013.
https://krebsonsecurity.com/2017/02/men-who-sent-swat-team-heroin-to-my-home-sentenced/
In the screenshot here, we can see Webb replying to a message from Gervais stating that "Edward has been terminated for leaking internal information to the competitors."
Wired cited experts saying it's unlikely Coristine could have passed a security clearance needed to view the sensitive government information he now has access to.
Want to learn more about Path? Check out the website https://pathtruths.com/