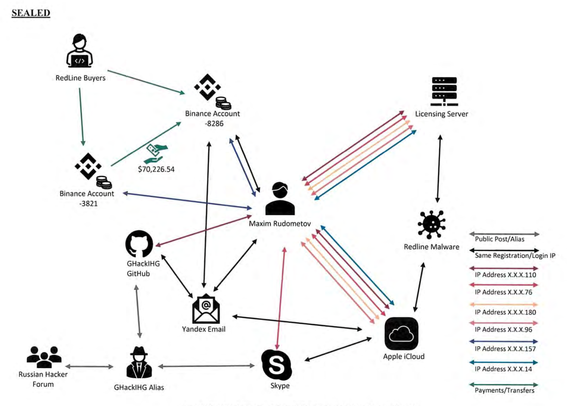
Logs often tell a story. Here's an interesting graph showing the how investigators linked Maxim Rudometov with allegedly administering the RedLine and META infostealers. First, he had a big setback not long after launching RedLine when another threat actor connected his previous nicknames he used underground forums. By soft doxing him, investigators were able to research identifiers related to those older nicknames. Essentially, his downfall was (as usual) the re-use of email addresses across various underground forums and legit services. Many roads in investigating cybercrime lead to big tech providers like Apple, Microsoft and Google where threat actors usually have accounts in their real names. Rudometov allegedly re-used an email address for his iCloud account, where investigators found RedLine's code. They also found a RedLine encryption key in his GitHub repo. The criminal complaint has other examples of risky OPSEC, such as using the same IP to administer RedLine as was used for gaming games, iCloud, etc.
#infosec