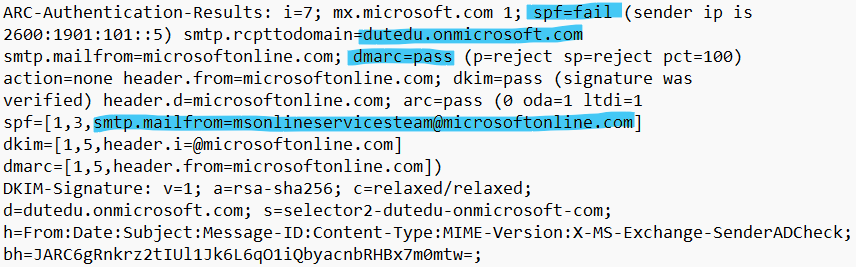
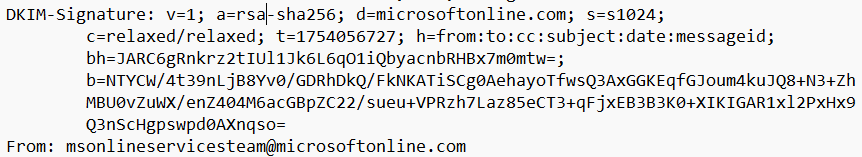
If you'd asked me before today if you could forge a legit Microsoft address on a scam message and have it pass DMARC I'd have said no way. But that just happened. Message originated from a malicious M365 tenant. Exchange Online added two DKIM sigs - the tenant’s MOERA domain and a valid d=microsoftonline.com platform signature. Because the forged From address also matched microsoftonline.com, DMARC passed solely on the platform DKIM, even though SPF failed multiple times. This is nuts; basically anyone can forge a microsoftonline.com address when sending from M365 infra. I now have a transport rule that bumps SCL on any message from microsoftonline.com with failed SPF and added 'microsoftonline.com' to domain impersonation protection in Defender.
When I was at school I had to learn a dead language (Latin). I hated it. Now having to learn a complex vendor-specific query language that is about as painful and probably soon to be about as dead. Timely comments from
@riskybiz, though I think perhaps not everyone is awake to the new reality yet!
Rather horrified to find that in order to install a phishing alert button, a certain popular security vendor requires this degree of access to organisations' emails:
I never knew London was such a fan of Vulcans but when visiting the cable-cars I came across a hundred-foot tall game of Kal-toh!
A rare photo of spidey as he awaits the arrival of his party guests…
This has got to be one of the most useful examples of AI: using nothing but a photo to analyse my diet.
Super creepy that Strava’s AI is scanning uploaded photos and making assumptions about my life. Can I have a “say less” button?
2 weeks to go. Still doable!
Another infuriating corporate
#securityawareness training message: "Don’t scan QR codes without verifying the URL! Tip: You can verify the URL of the QR code or link by hovering over it." This is a prime example of how we blame people for a lack of technological controls. I would submit that it's impossible to recognise whether a QR code is malicious based on just the domain name when many use redirect domains (a benign example shown below from a kids book which has a domain in print beneath the code but it links to a redirect). A phone will not show you the ultimate destination so 'hovering' over the code isn't helpful. The reason of course is that if you're printing a QR code for long-term access you're going to want to control where that redirects to in case the destination changes. We should fix this with a technology change; having QR-scanning devices identify 302 redirects and follow them to present the actual destination domain on screen, then automatically check that against a URL reputation service to prompt the owner when it's risky. Is that so difficult to achieve that our best alternative is dumb advice?