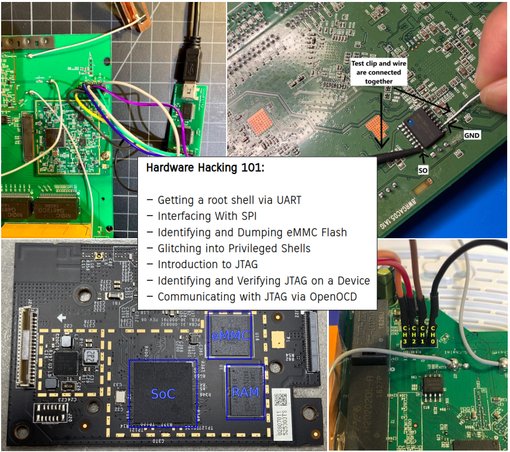
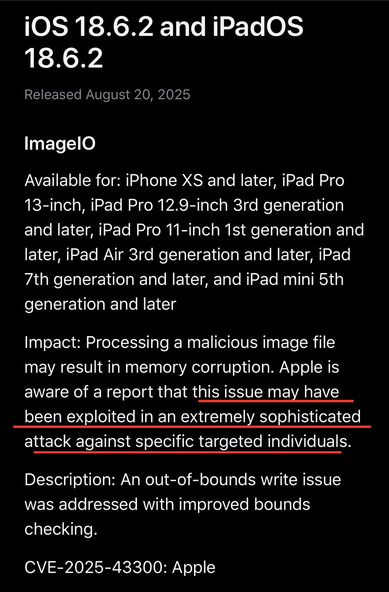
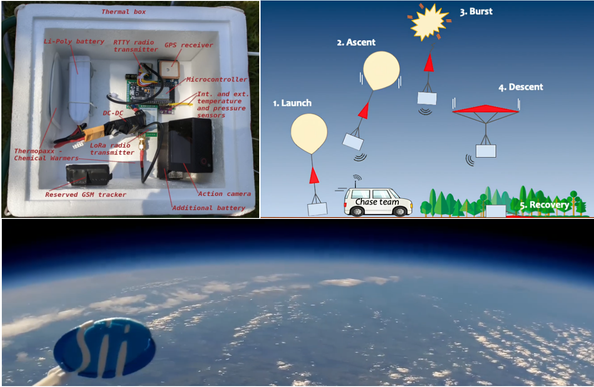
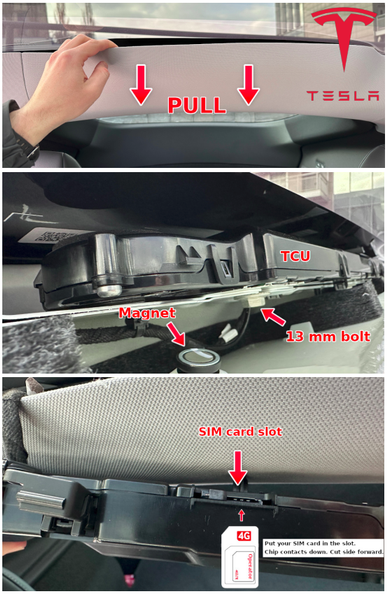
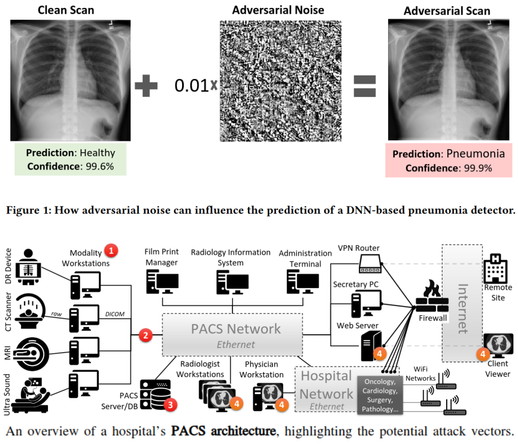
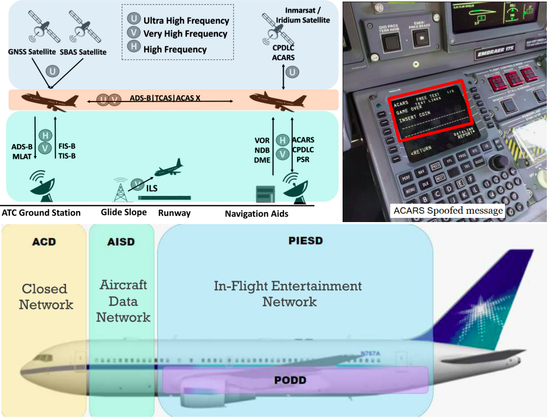
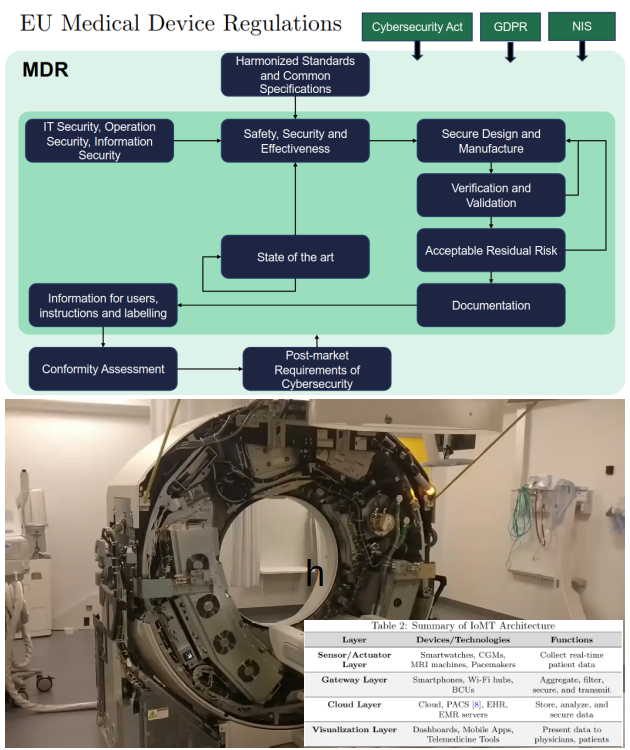
Hardware Hacking 101: A series of great hands-on articles about JTAG, UART, SPI, and hardware glitching. 👩🏻💻📟🛠️⚡️🎓
More details on:
LinkedIn: https://www.linkedin.com/posts/dlaskov_cybersecurity-infosec-technology-activity-7366497166942449665-SKO1
Substack: https://it4sec.substack.com/p/hardware-hacking-101-a-series-of