Ivan Fratric
@ifsecure@infosec.exchange
- 1,042 Followers
- 33 Following
- 34 Posts
Security researcher at Google Project Zero. Views / opinions are my own.
@CodingThunder The talk was recorded, but it was given in Croatian.
In my recent conference talks on browser security, I showed a calc-popping exploit demo that targets Firefox 135.0. For educational purposes, to try to demistify some of that calc popping magic, the demo code is now public https://project-zero.issues.chromium.org/issues/389079450#comment7
Last week, I gave a talk on web browser security research at a student-organized conference. I tried to make the talk reasonably beginner-friendly, so the slides (linked here) could hopefully be useful to someone as a learning resource. https://docs.google.com/presentation/d/1rEPiqV0KBHAI0lVym283OHzYRXNCCuGudmDby1Z1qyc/edit?usp=sharing
@z 😞
@freddy Ah, sorry that it came across like that.
@freddy Thanks and it was great to meet you in person! I know about that implementation, it's based on the suggestion I made on bug 1951008 (see comment #6) :)
...and now the video of my talk "Finding and Exploiting 20-year-old bugs in Web Browsers" is live too https://www.youtube.com/watch?v=U1kc7fcF5Ao

OffensiveCon25 - Ivan Fratric - Finding and Exploiting 20-Year-Old Bugs in Web Browsers
The slides for my OffensiveCon talk "Finding and Exploiting 20-year-old bugs in Web Browsers" https://docs.google.com/presentation/d/1pAosPlKUw4uI5lfg7FVheTZAtI5mUy8iDeE4znprV34/edit?usp=sharing
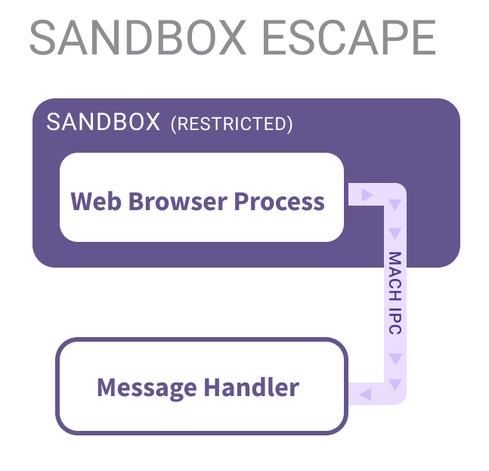
Thrilled to announce my new Project Zero blog post is LIVE! 🎉 I detail my knowledge-driven fuzzing process to find sandbox escape vulnerabilities in CoreAudio on MacOS.
I'll talk about this and the exploitation process next week
@offensive_con
https://googleprojectzero.blogspot.com/2025/05/breaking-sound-barrier-part-i-fuzzing.html
I found 2 use-after-free bugs in libxslt with Jackalope, let's find more together! The harness is now included in examples (link below). This also serves as a demo for two not very commonly used modes in Jackalope: grammar mutational fuzzing and sanitizer coverage.
https://github.com/googleprojectzero/Jackalope/tree/main/examples/libxslt
https://github.com/googleprojectzero/Jackalope/tree/main/examples/libxslt