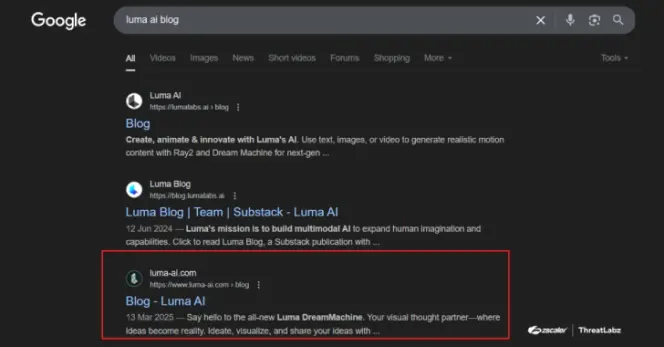
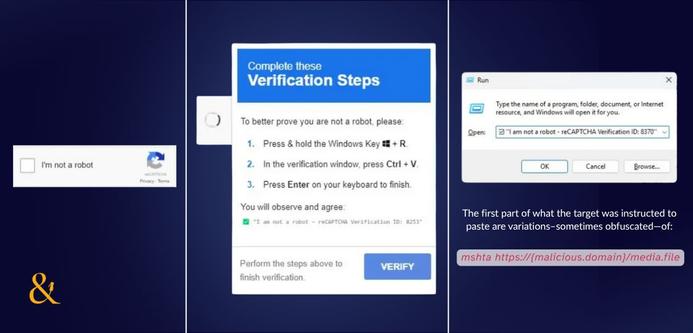
⚠️ The Hacker News just spotlighted a growing threat: SEO poisoning campaigns delivering malware through fake tool websites.
Attackers are mimicking trusted apps like PuTTY, Zoom, and ChatGPT, pushing them high in search results. Over 8,500 SMB users were targeted in just four months.
The article breaks it down clearly. If you haven’t read it yet, it’s worth your time.
Read it here: https://thehackernews.com/2025/07/seo-poisoning-campaign-targets-8500.html