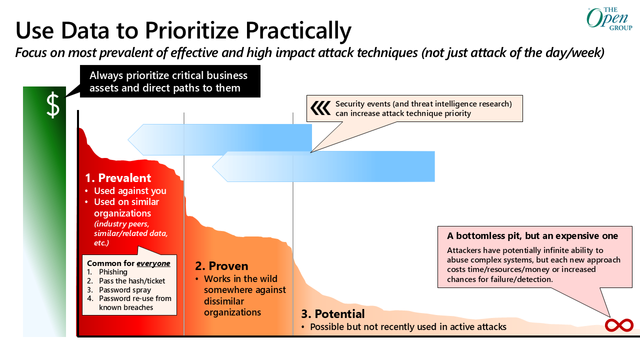
Are you focusing on the important parts of cybersecurity first?
It's critical to ruthlessly prioritize in cybersecurity because there is an infinite number of ways that attackers could possibly attack your systems.
What you need to spend time thinking about is what is easiest and most effective for the adversaries, not what is possible.
You can use the 3 P's to remember what to focus on first:
1. Prevalent
2. Proven
3. Possible
Never go to the next stage until you are done with the first stage.
If you are tempted to research that cool new technique you just heard 'nation state X' did against a high profile target but you haven't effectively mitigated password spray or pass the hash, STOP!! 🛑⛔🚫🛑🛑!!!
…go back and take care of those basics before wasting your precious time and effort on something that is likely not to affect you.
The attacks you will see most are the ones that will get the job done easiest and most reliably for attackers:
1. Attackers will prefer prevalent well-known methods with a successful track record
2. They will fall back on other proven methods that are also likely to work
3. …and most will explore other potential options if needed (and if they have the skills/resources/funding/etc. to develop those into usable attack methods).
This slide visual is from the upcoming Security Matrix standard from The Open Group that captures this implication.
For a copy of this slide, see the downloadable MCRA deck - https://aka.ms/MCRA
For a webinar discussing the security matrix and other current and upcoming standards from The Open Group, see https://aka.ms/TOG-standards