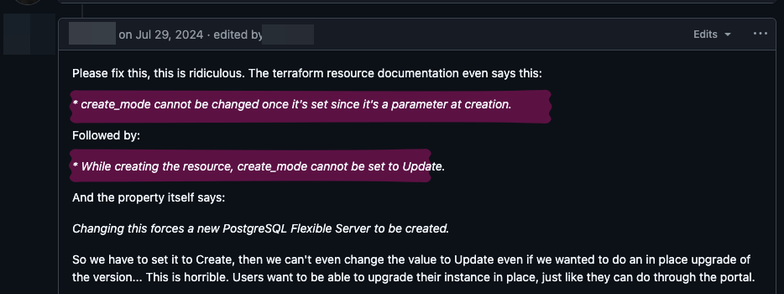
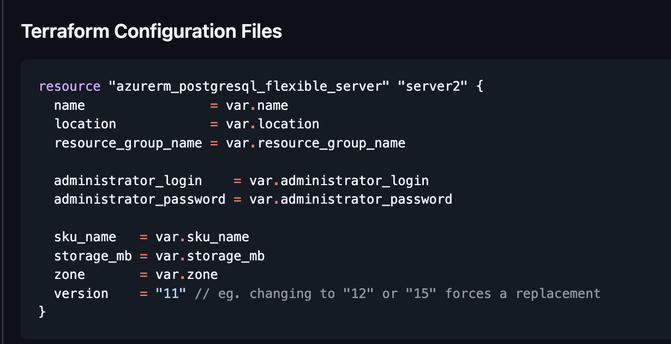
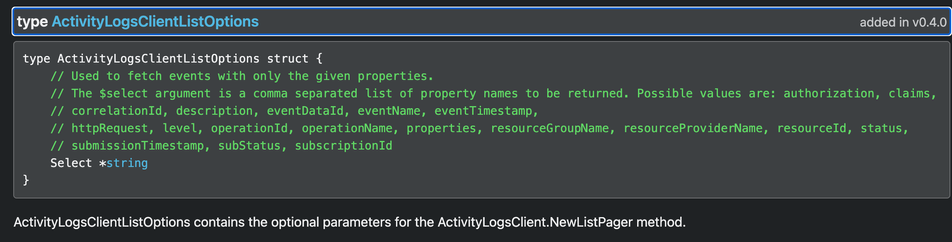
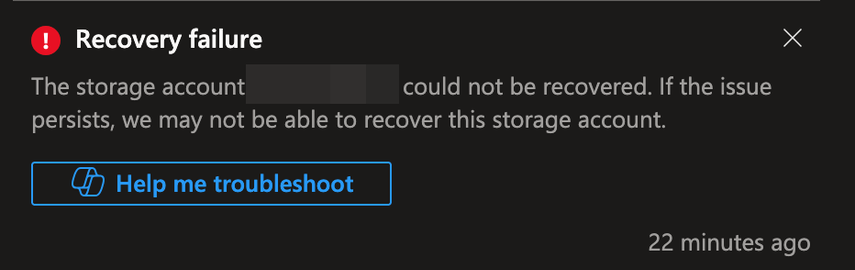
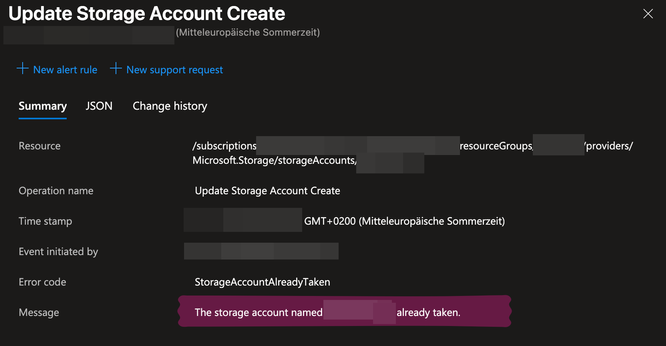
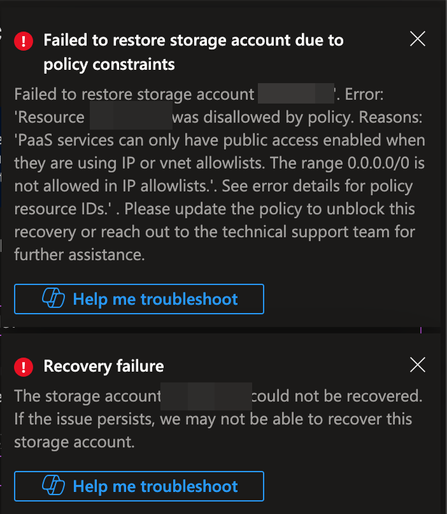
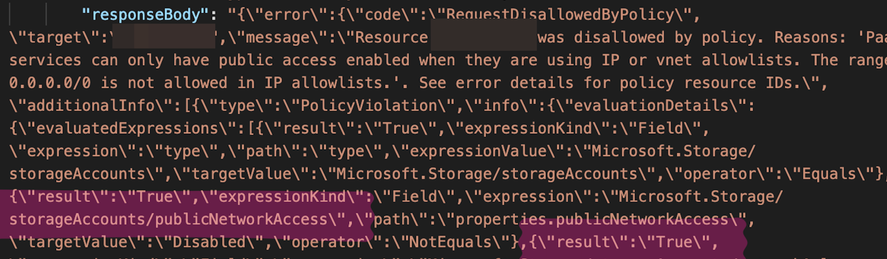
Day 484. Continuing the shit from day 483, when you want to upgrade the version of your #Azure Database for PostgreSQL flexible server through #Terraform without wiping it, you have to set the 'create_mode' property to 'Upgrade' instead of 'Default'. However, you cannot set it to 'Upgrade' when creating the resource and changing it later forces a replacement of the resource, wiping all of your data.
Daily dosis of shit experienced on Microsoft Azure.
This account is obviously not affiliated with Microsoft.
| Short | https://azsh.it |
| Short Example | https://azsh.it/45 |