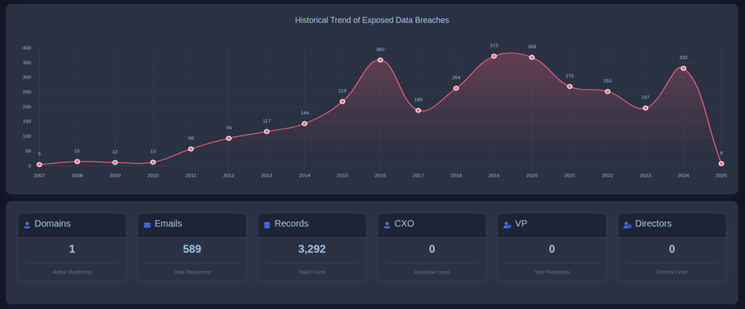
@XposedOrNot += InflateVids Data Breach
The InflateVids #databreach in December 2023 exposed over 13K unique email addresses along with usernames, IP addresses, genders, and passwords stored as SHA-1 hashes. The breach impacted users of the inflatable and balloon fetish videos website.
Exposed data: Email addresses, Usernames, IP addresses, Genders, SHA-1 hash passwords
Potential risks: Privacy breaches, Identity exposure, Unauthorized access