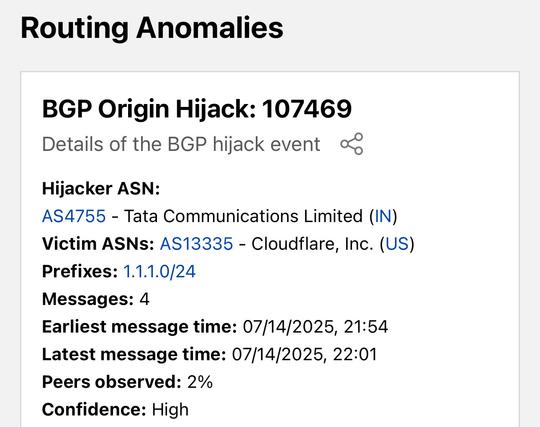
@aly @GossiTheDog @ssamulczyk Sure! So Tata (insert reason X) decided to tell the world they were the way to get to 1.1.1.0/24 network, which includes the host 1.1.1.1, Cloudflare's DNS IP. And so the internet listened to Tata and starting updating everyone that they should start sending all the requests for 1.1.1.1 via Tata's network INSTEAD of Cloudflare who is the owner of that "network prefix". There are nerd knobs to turn and encryption which can prevent this, but after literal decades still hasn't been done.
This kind of thing happens much less than the past, but the effects are much larger as the internet is much larger now. Malicious actors like to do it for profit.
For more technical details, this article does a good job explaining: https://www.kentik.com/kentipedia/bgp-hijacking/
https://blog.cloudflare.com/cloudflare-1-1-1-1-incident-on-july-14-2025/

Cloudflare 1.1.1.1 Incident on July 14, 2025
On July 14th, 2025, Cloudflare made a change to our service topologies that caused an outage for 1.1.1.1 on the edge, resulting in downtime for 62 minutes for customers using the 1.1.1.1 public DNS Resolver as well as intermittent degradation of service for Gateway DNS. We’re deeply sorry for this outage. This outage was the result of an internal configuration error and not the result of an attack or a BGP hijack. In this blog post, we’re going to talk about what the failure was, why it occurred, and what we’re doing to make sure this doesn’t happen again.