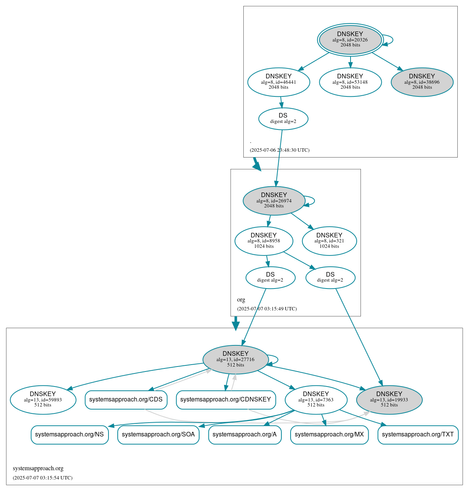
Over the last year-plus we have been working on a new book focussing on network security. Most recently we have been looking into the security of the Internet's infrastructure, including the domain name system (DNS). Even though attacks on DNS have been known since the 1990s, efforts to secure it have been limited in their adoption. For this week's newsletter, we enabled DNSSEC (DNS security extensions) on our domain and it was remarkably painless. Yet DNSSEC adoption remains sluggish, for reasons that are explored in the newsletter.
https://systemsapproach.org/2025/07/14/does-dns-security-matter/
🧵
1/n