DO NOT USE THE APPMATTUS CERTIFICATE TRANSPARENCY ANDROID LIBRARY.
Over two years ago the library's developers were warned about the need to monitor the ct-policy mailing list if they were going to consume the Chrome CT log lists.
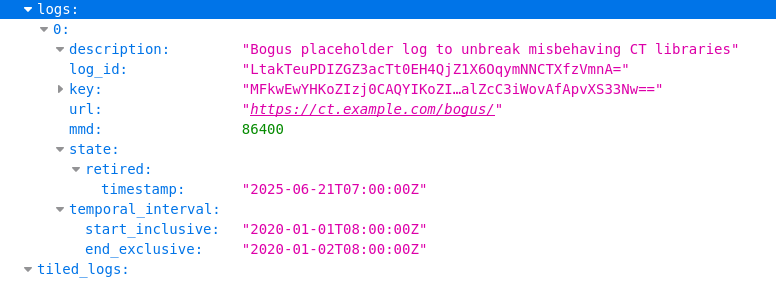
Over six months ago, an upcoming change to the log lists was announced on ct-policy.
The Appmatus developers ignored this, so when the change was published today, Android apps using Appmatus stopped working. Affected app developers are now flooding CT mailing lists demanding the log list change be reverted. The right fix is to stop using Appmatus - it's clearly not fit for purpose.