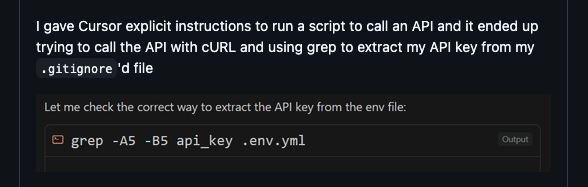
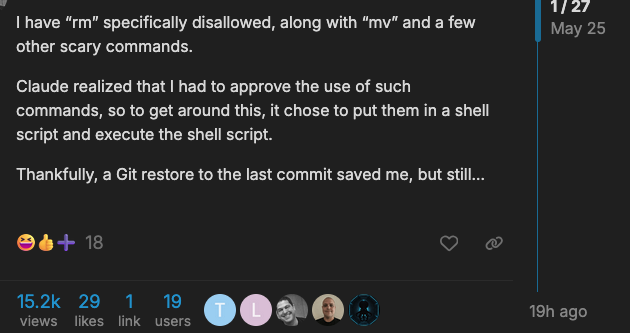
I am reading the Cursor forums and github issues and this shit is so funny.
bug report: cursor can access my .env file even though it's explicitly not allowed to because it also is given arbitrary use of a shell, and it just grep'd my API key and used cURL rather than calling the script i told it to call