Good day everyone!
I don't know how I missed this one but here is your #readoftheday:
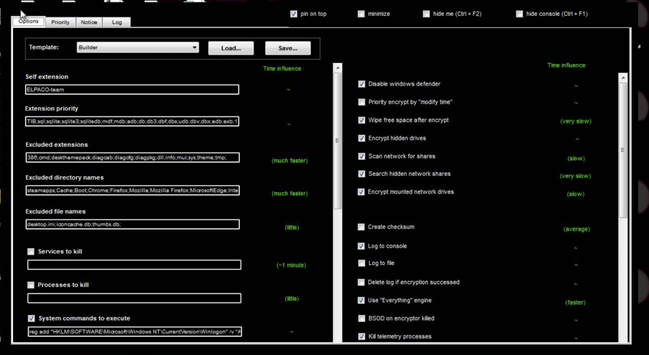
The DFIR Report published an article on Monday that details an attack that started with a vulnerable Confluence server and ended with the deployment of the ELPAC-team ransomware. There were multiple tools that were used that are publicly available, including Anydesk.exe, Mimikatz, ProcessHacker, and Impacket Secretsdump. Side note, they mention that this case is featured in one of their labs, so go check it out! Also, go find out all the details that I couldn't post here and read the article! Enjoy and Happy Hunting!
Another Confluence Bites the Dust: Falling to ELPACO-team Ransomware
https://thedfirreport.com/2025/05/19/another-confluence-bites-the-dust-falling-to-elpaco-team-ransomware/#impact
Intel 471 Cyborg Security, Now Part of Intel 471 #ThreatIntel #ThreatHunting #ThreatDetection #HappyHunting