After installing April's updates, Windows 10 and 11 systems now have an empty C:\inetpub directory.
This seems... unexpected?
After installing April's updates, Windows 10 and 11 systems now have an empty C:\inetpub directory.
This seems... unexpected?
So, apparently this is the "fix" for CVE-2025-21204. Microsoft recently updated their advisory to say what the update does.
Prior to everybody freaking out, the advisory for CVE-2025-21204 said nothing about what it does.
Two gripes:
C:\. They refused to make any change because it might "break things".Great job, folks.
Would changing the ACLs to not allow non-admin users the ability to create directories off of C:\ really have a real-world impact of limiting LPEs?
Absolutely. When you write a tool to look for things (e.g. Crassus), you see things. Heck, I've seen a privileged service attempt to open files in C:\Program%20Files\, which any non-admin Windows user can create by default.
But no, even despite being presented with evidence for how this could fix an entire CLASS of LPEs on Windows, MSRC was not interested.
From over at the Bad Site ™
Both the vulnerability and the "fix" for CVE-2025-21204 are quite silly.
The scenario is:
C:\inetpub\wwwroot directory and puts web content thereThe outcome is:
The web content provided by the non-admin user (be it a web shell or whatnot) is served up by IIS.
Maybe non-admin users shouldn't be able to make directories or junctions (to directories or files) in C:\?
NAH.
Maybe installing IIS should provide a clean webroot when it's installed?
NAH.
Just preemptively make a C:\inetpub directory that non-admin users can't write to. That fixes the problem. 🤦♂️
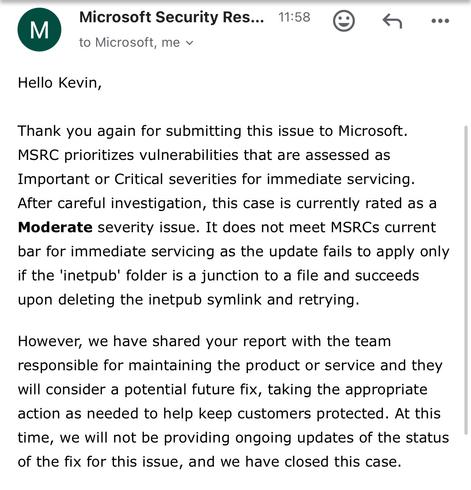
Attached: 1 image Microsoft have rated the ability for non-admin users to stop Windows patching as a moderate issue and closed the case. EDR providers, including Microsoft, probably want to add signatures for junction points from \inetpub being created on boot drive as it doesn’t look like this will be fixed any time soon.