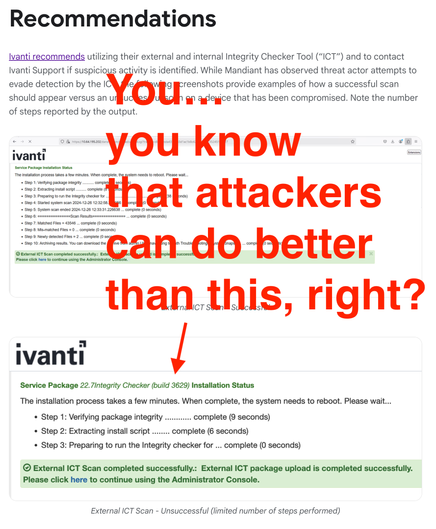
As per usual, watchTowr has an excellent writeup on the vulnerability.
https://labs.watchtowr.com/do-secure-by-design-pledges-come-with-stickers-ivanti-connect-secure-rce-cve-2025-0282/
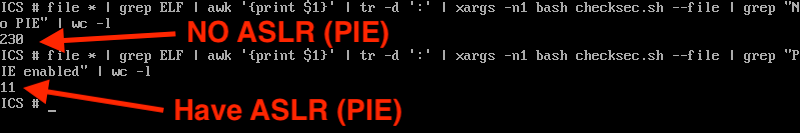
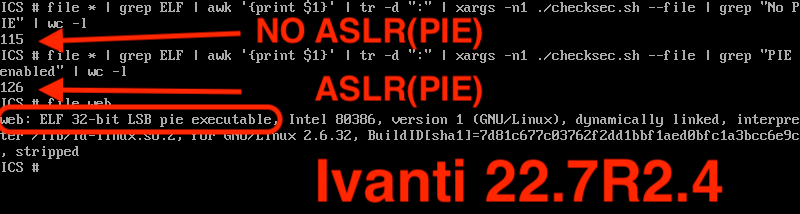
As they mention, the clear thing that has changed is the web binary, which indeed is ASLR'd via PIE.
If "web" is the process that's being exploited, we should be protected with ASLR, right? Well, sorta.
First, let's look at the most recent builds (22.7R2.4 or R2.5) of ICS. As it turns out, they are getting better with enabling PIE. It's now over 50% of the executables in /home/bin. My prior screenshot was from a 22.6 version of the appliance. Baby steps?
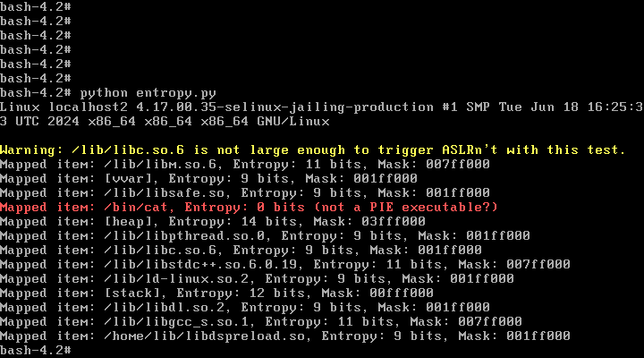
While the ICS has a 64-bit kernel (that is over 6 years old), this web server binary (as well as every other binary in /home/bin) is 32-bit. What does this mean for ASLR? Well, by my calculation, that gets us about 9 bits of entropy. Which, depending on what the exploit does, could be able to be brute forced.
There's no use of pesky stack canaries either, so Ivanti has made it easier for those looking to exploit stack buffer overflows.