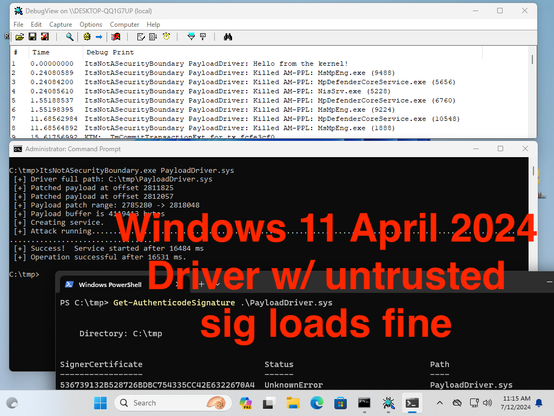
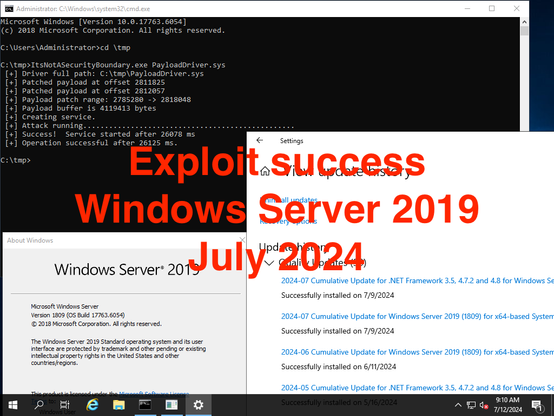
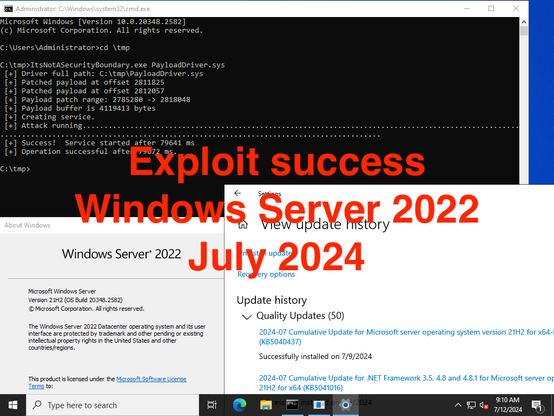
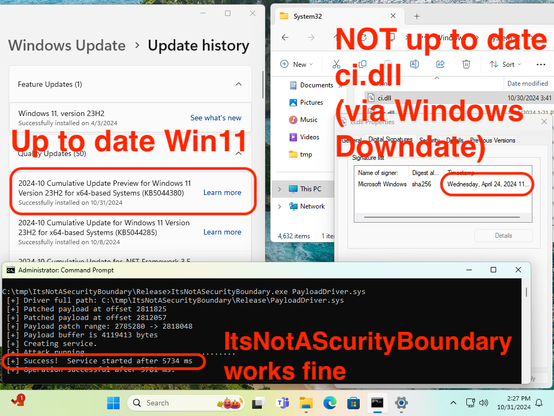
Excellent work from @GabrielLandau on how Windows can be tricked into loading drivers with untrusted signatures:
https://www.elastic.co/security-labs/false-file-immutability
Repeat after me:
"Windows admin to kernel is not a security boundary"
"Belief in BYOVD protection is fantasy"
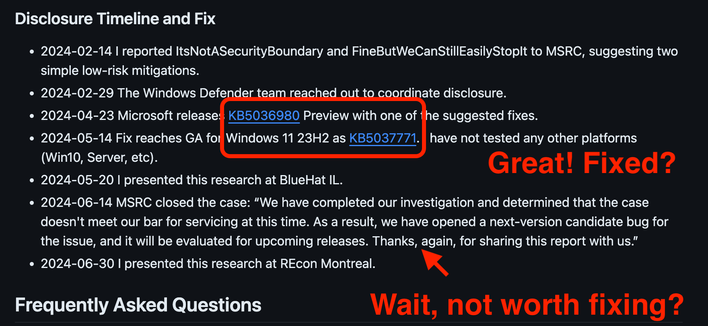
MS seems to have mitigated the attack with May's updates for Windows 11, but at the same time they haven't assigned a CVE or have mitigated the issue for Windows Server because it's not a security boundary.
Some more details on this non-boundary:
https://vu.ls/blog/byovd-protection-is-a-lie/
https://vu.ls/blog/byovd-protection-is-a-lie-pt2/