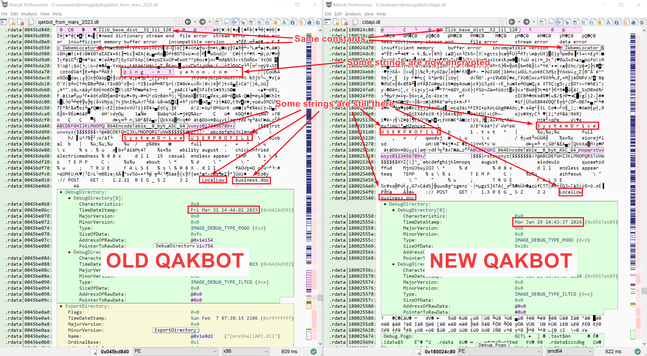
#Qakbot came back with new tricks. In this new blog post, we will:
● unpack it
● decrypt it (strings + cnc)
● and write a config extractor in python
using only static analysis (and #malcat of course :). Link:
https://malcat.fr/blog/writing-a-qakbot-50-config-extractor-with-malcat
Writing a Qakbot 5.0 config extractor with Malcat
Starting from a (backdoored) MSI installer, we will unroll the infection to chain to get the final Qakbot sample. Sticking to pure static analysis, we will then decrypt Qakbot's configuration and finally write a script in Malcat to automate the process.