Integrated circuits, chips, and silicon... Yesterday I was on site at a client’s headquarters, and the owner asked me a question that took me completely by surprise. He asked, “How are ICs and chips related? What does one have to do with the other? And where does silicon fit in?”
As a college professor, through painful experience, I developed a concept I call the Common Body of Knowledge. The Common Body of Knowledge includes those things my students will already know when they attend class. I don’t have to teach these things. For example, when explaining this to my students, I’ll ask, “What is the name of the ocean on the east coast of the USA?” My students just sit there, and I have to encourage them by saying, “It’s not a trick question. The answer is as easy as you think it is. I’m trying to teach you a concept, and this illustration will help.” Finally, one or two brave souls will say, “The Atlantic.”
“Yes! That’s it! You see, that’s in the Common Body of Knowledge. Now, here’s the problem I run into as your instructor: sometimes, I’ve known something for so long that I just assume it’s in the Common Body of Knowledge. But it actually isn’t. Someone had to teach me this ‘thing,’ somewhere in my distant past. I’ve known it so long I don’t even remember learning it. Now, during class, I may casually mention something like everyone knows it, and I’ll just go on to the next thing. I’m counting on you to stop me. Raise your hand. Ask the question. Because if you don’t know what I just said, there’s a very good chance that some other people in the class don’t know, either.”
I look around the class, and make eye contact with as many students as possible. “I want you to be the brave one. Ask the question. That’s how I will learn that something I said is NOT in the Common Body of Knowledge, and I need to back up and add it to the class session.”
Now, back to the opening of this post. My client was hearing things in the news, and asked me to explain chips, ICs, and silicon. I had no idea this wasn’t in the Common Body of Knowledge, but it’s not. People have to learn it.
Here now, for you, is a brief explanation.
SILICON
Silicon is a special element with remarkable chemical properties. It doesn’t conduct electricity easily, like gold or copper. But it’s also not an insulator, like rubber or pure water. Silicon is a semiconductor. We can make it conduct electricity, or stop conducting electricity, by mixing silicon with other chemicals and applying various voltages to it. This is the heart of all electronic parts now. Conducting or not conducting. On or off. One and zero.
CHIP
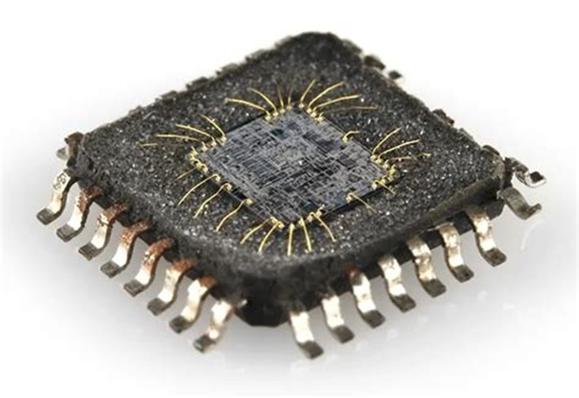
Through a complex manufacturing process, we combine a bunch of these little on/off junctions on a very tiny piece of silicon. This piece of silicon is a flat “chip” of a silicon rock.
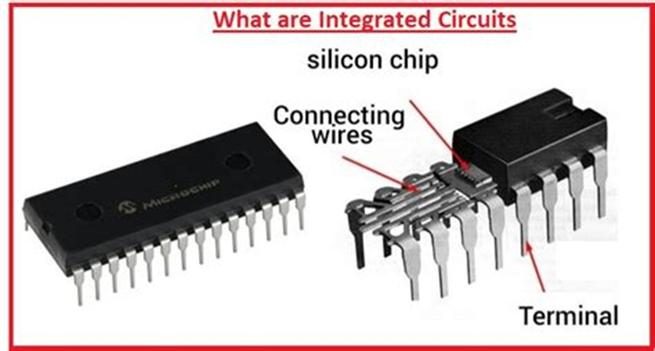
INTEGRATED CIRCUIT
Infinitesimal gold wires are attached to various points on the chip to apply voltages. The tiny gold wires then connect to larger metal pins that can be attached in various ways to a circuit board. The assembly of the chip, the gold wires, and the pins is enclosed in a plastic or ceramic housing. This package is rugged enough to be shipped and sold as an integrated circuit, or IC.
SLANG USAGE
The terms “chips” and “ICs” are used so interchangeably that you can now forget everything I said about a distinction between the two. The little piece of silicon is an integrated circuit. The entire package is a chip. There is no problem with using either term in common conversation.
SUPPLY CHAIN THREAT
Question: who controls the design and manufacture of the chips? It’s possible for a malicious manufacturer to put extra circuitry in the package to do whatever they want it to do. This is why the manufacture of silicon integrated circuits is so important. You should buy chips from “friendly” manufacturers you can trust.
I hope this helps you understand what you’re reading in the financial news about the sourcing and manufacturing of electronics parts.
#IntegratedCircuit #ASIC #Silicon #SupplyChain #IC #ChipManufacturing