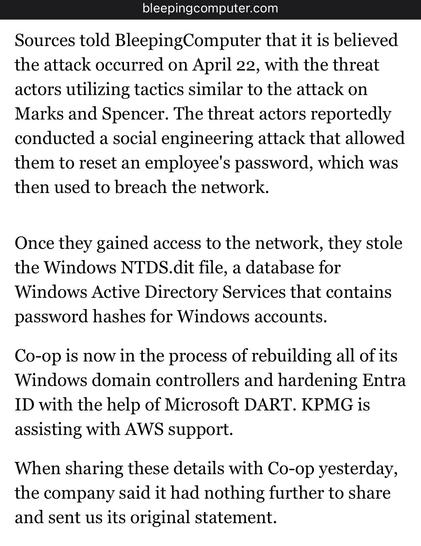
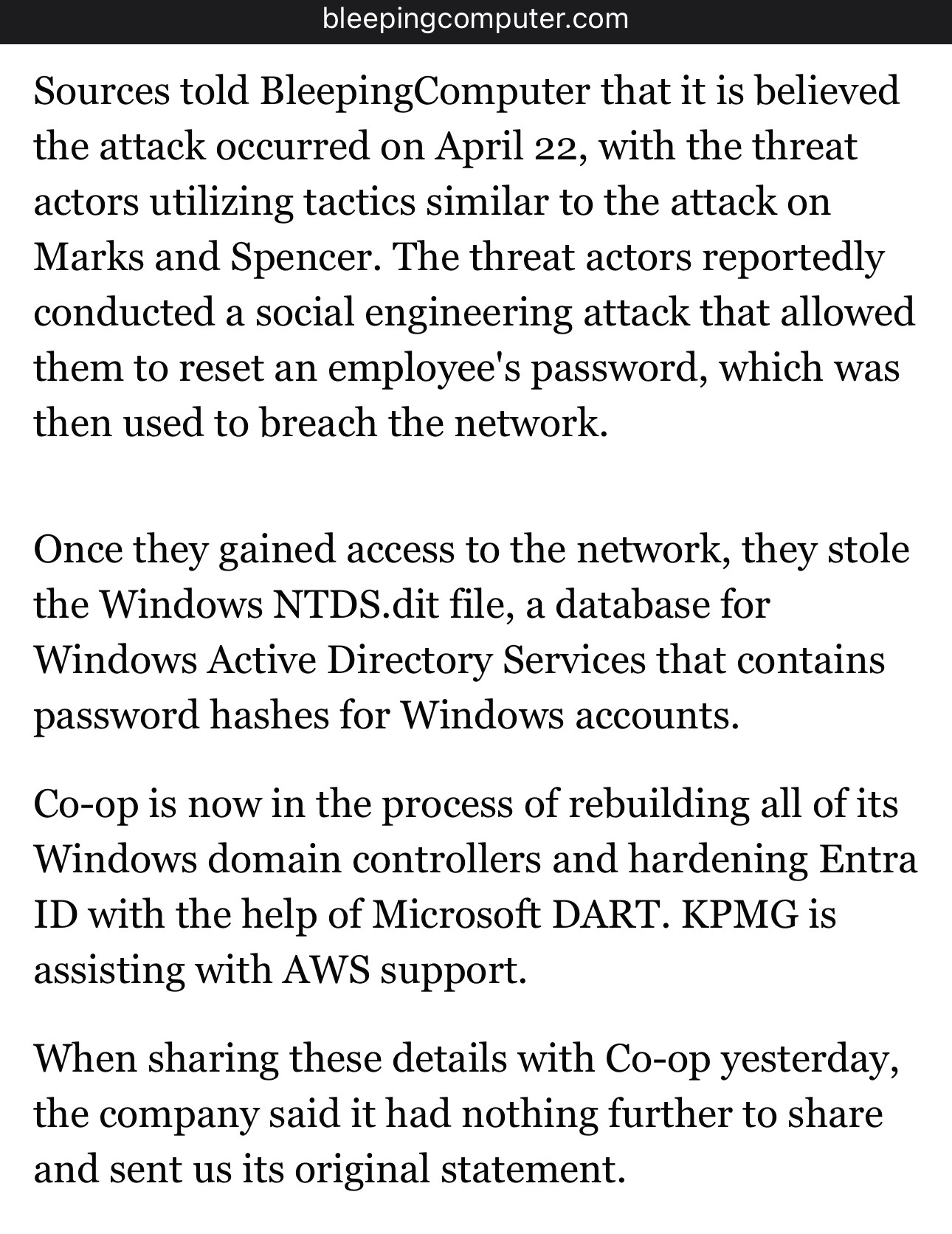
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
One of M&S’ biggest suppliers have said they have reverted to pen and paper for orders due to M&S lacking IT.
Additionally, M&S staff are raising concern about how they will be paid due to lack of IT systems.
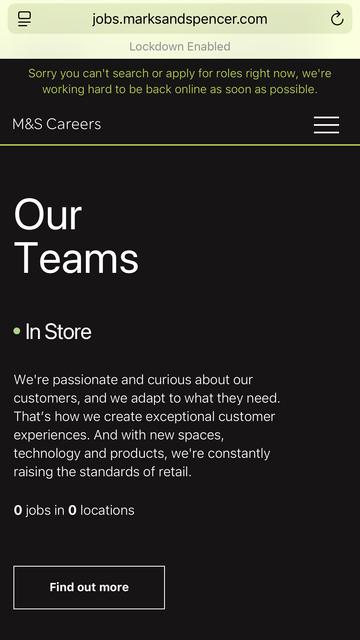
M&S are over a week into a ransomware incident and still don’t have their online store working.
Here's the ITV News report anyhoo, logline: "ITV News understands the the ongoing cyberattack faced by the supermarket has worsened since Friday, impacting the ordering system, drivers and warehouse staff."
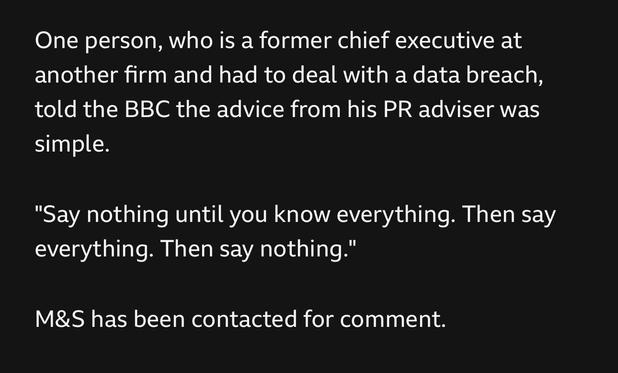
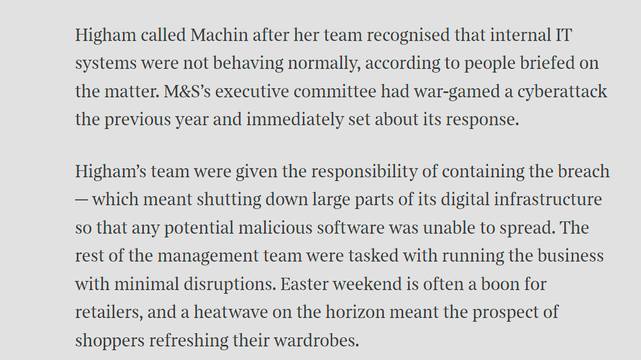
Sunday Times has a piece looking into ransomware incident at Marks and Spencer. It's pretty good, goes into their contain and eradicate focus.
"By shutting down parts of the IT estate, Higham’s team had worked to prevent the attack from spreading, but had also stopped parts of its digital operations from functioning. This was considered a worthy trade-off."
One error in the article - lack of recovery doesn't mean no ransomware paid. Paying is not quick restoration.
https://www.thetimes.com/business-money/companies/article/m-and-s-cyber-attack-ms-klrnxvwq6
Great NCSC piece by @ollie_whitehouse
I’d add - block by Entra policy specifically High risk logins (below is too FP prone), and SOC monitor them. SOC playbook = account probably compromised. How?
https://www.ncsc.gov.uk/blog-post/incidents-impacting-retailers
Sky News quote a source in M&S head office saying Marks and Spencer have no ransomware incident plan so they are making it up as they go along apparently, with staff sleeping in the office and communicating via WhatsApp.
M&S dispute this, saying they have robust business continuity plans.
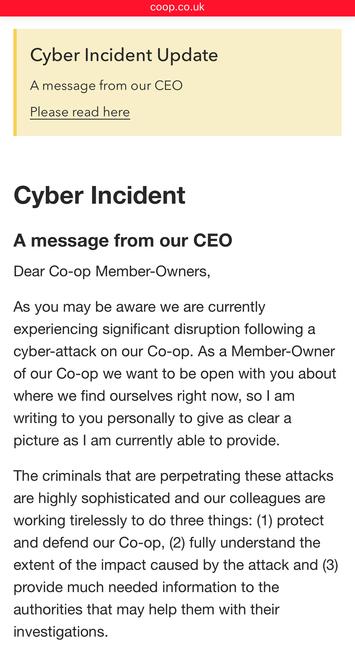
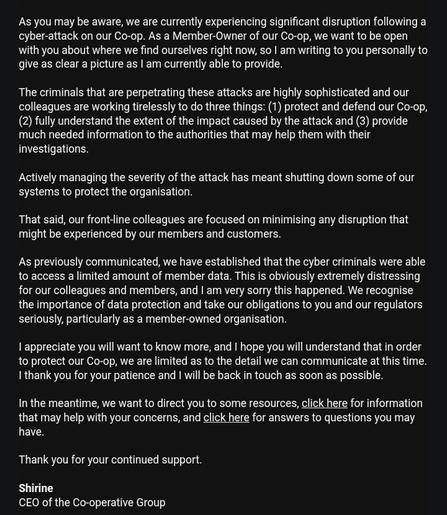
Co-op Group appear to be trying to course correct with their cyber incident comms.
They’re calling it a cyber incident now, and have put a statement on the front page of their website, along with an FAQ. They haven’t yet emailed members (they should). Edit: they’ve started emailing members.
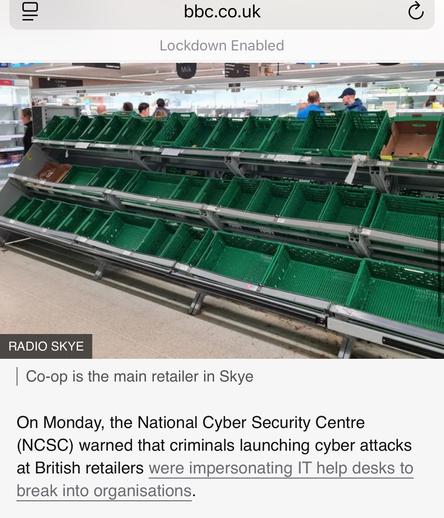
People are also taking to social media to post pictures of apparently emptying store shelves.
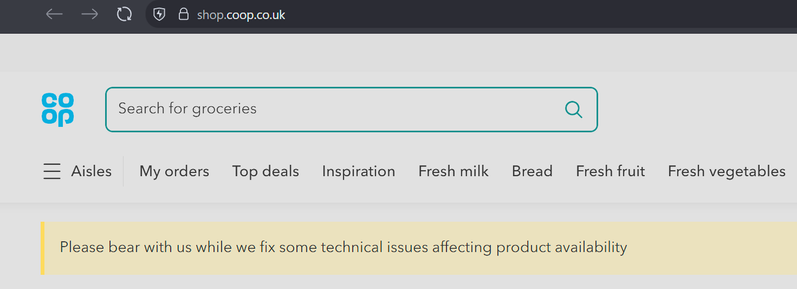
The Co-op website claims it is down to "technical issues".
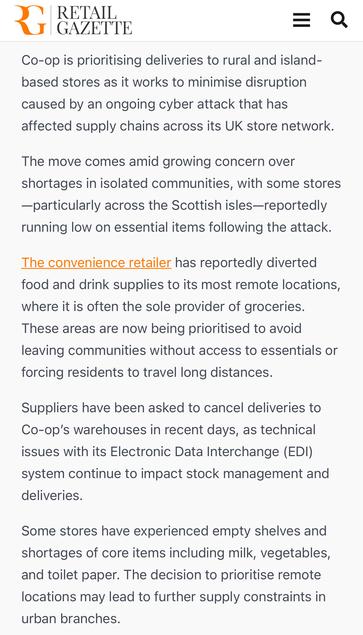
Co-op Group are redirecting supplies from their urban stores to remote and island locations due to stock shortages.
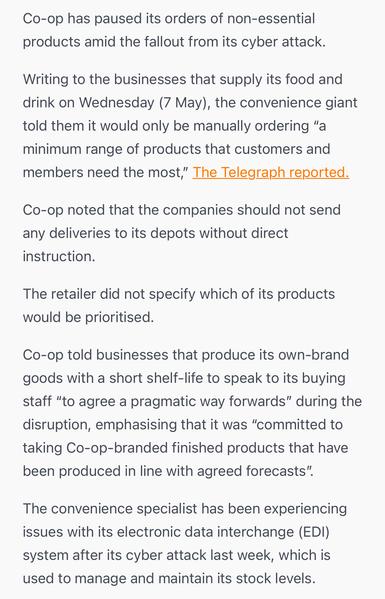
The article mentions their EDI platform is suffering “technical issues”. https://www.retailgazette.co.uk/blog/2025/05/co-op-reroutes-stock/
I just did a Shodan Safari on Co-op - basically all their Windows and Linux systems in their core DCs at network boundary are down, it's not just EDI. It's been like that for just under a week, prior to that things were still online.
I feel really bad for them as it's a great org. Also their CEO is basically the only one who stood up like this for trans people.
https://www.telegraph.co.uk/business/2025/05/04/ill-protect-trans-people-to-the-end-vows-co-op-boss/
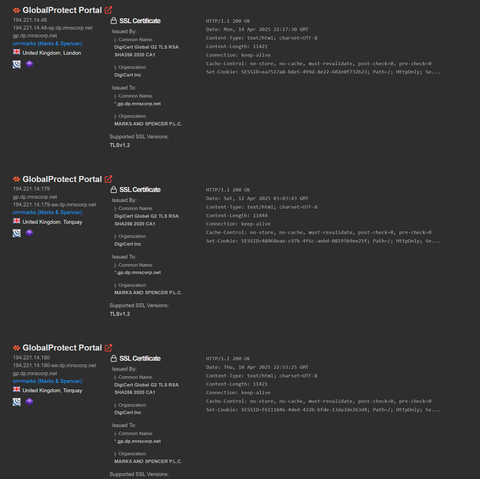
If you're wondering about Marks and Spencer - I just did a Shodan Safari of their network boundary, Palo-Alto GlobalProtect VPN remote access access is still offline, 15 days later.
Online orders are still not working, and the store stock checker is disabled now.
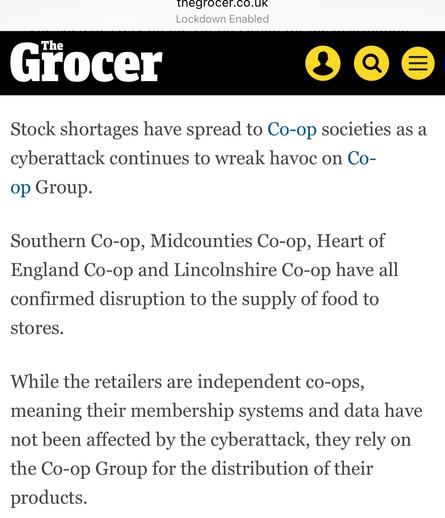
The Grocer reports 4 regional Co-ops, who aren’t part of Co-op Group, are suffering stock shortages as they are supplied by Co-op Group.
They expect customers to start to see availability issues on shelves in the coming days.
For orgs looking for defence tips for the attacks on UK retailers, this blog from 2022 about the UK teenagers in LAPSUS$ has relevance.
As a plot twist - not documented anywhere online, but LAPSUS$ first attacks in 2021 were against UK high street retailers.
DEV-0537 criminal actor targeting organizations for data exfiltration and destruction | Microsoft Security Blog
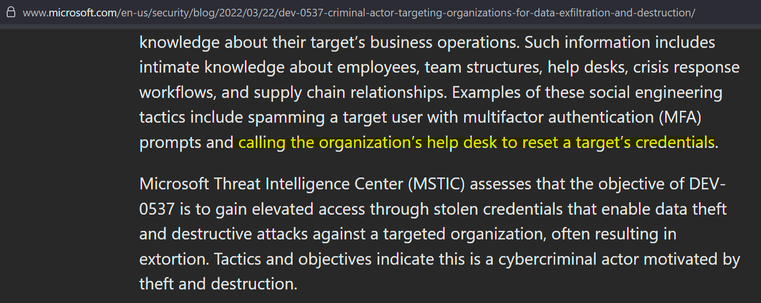
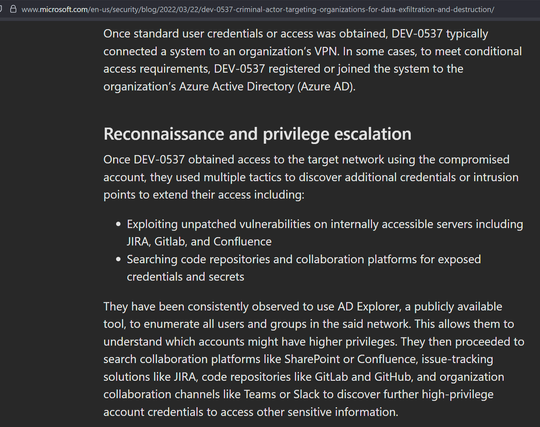
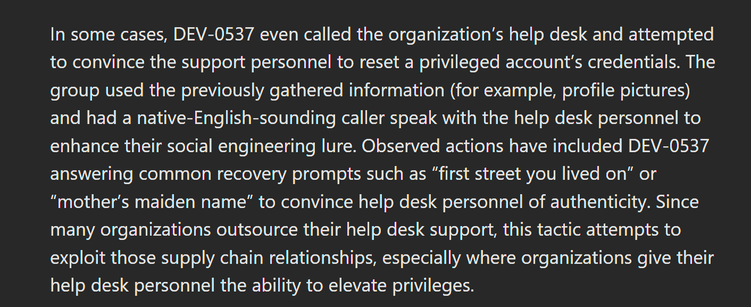
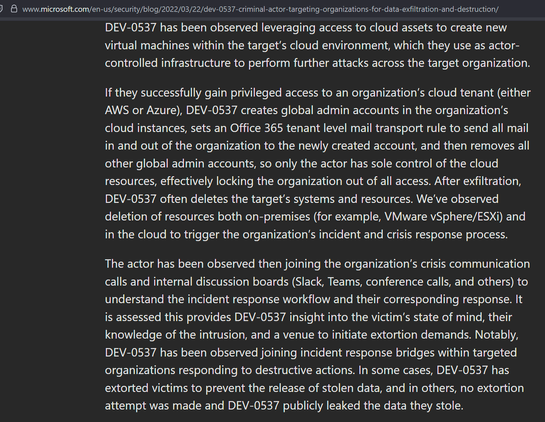
The activity we have observed has been attributed to a threat group that Microsoft tracks as DEV-0537, also known as LAPSUS$. DEV-0537 is known for using a pure extortion and destruction model without deploying ransomware payloads.
Co-op Group have provided some more detail about what it’s doing about remote lifeline stores (ones where they’re the main/only retailer on an island):
“From Monday, 12 of the most remote lifeline stores will receive treble the volume of available product, and another 20 lifeline stores will get double the volume.” https://www.bbc.com/news/articles/c071e7x80djo
This ITV News report linking the Co-op and M&S breaches to SIM swapping is not accurate, no source given. https://www.itv.com/news/2025-05-12/sim-swap-fraud-rises-by-1000-as-criminals-exploit-two-factor-authentication
They also have a report today saying Co-op stores are restocked, which is also not accurate - that one is sourced from Co-op, but obviously doesn’t stack up to looking in Co-op stores.
If anybody is wondering, all of Marks and Spencer's Palo-Alto GlobalProtect VPN boxes are still offline, 3 weeks later. Pretty good containment method to keep attackers out.
Co-op's VDE environment is still down, too.
https://cyberplace.social/@GossiTheDog/114399017367179104
@GossiTheDog Incident response specialists the world over wince into their keyboards.
This is another object lesson in how not to do it. It'll be taught to students in future.
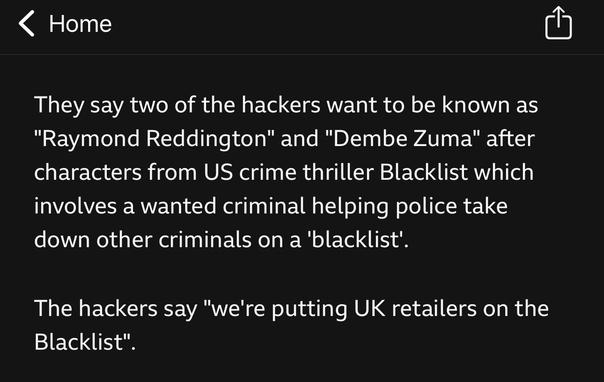












 🌬️
🌬️

